Your Trusted Partner in Comprehensive
Information Security Services
Safeguard your Products and Applications with our cutting-edge Information Security Services.
Resources
Certified on ISTQB
CEH Certified InfoSec Professionals
SME on Automation
Number of Projects Delivered
Verticals Served
Countries clients located (USA, Australia, Europe etc.)
In an era of constant digitization, maintaining reputation credibility is paramount. However, even the most sophisticated security measures may fall short against ever-evolving cyber threats.
Evoke Technologies’ Application Security services can benefit you with the knowledge, expertise, and efficiency for a thorough security evaluations of your applications and environments. Our assessment services go beyond automated tools and offer a comprehensive solution to secure your applications and supporting systems.
Our comprehensive application security services can transform your enterprise into one with advanced and effective application security. Our experts deliver detailed security assessments that extend beyond automated tools, providing a clear view of the security state of applications and supporting systems, along with the optimal path to remediation.
Industries We Serve
Service Offerings
Dynamic Application Security Testing (DAST) – Automated Scans and/or Manual Pentests
DAST services that reveal critical vulnerabilities like XSS, SQLi, CSRF, and hidden misconfigurations undiscovered by conventional tools.
Static Application Security Testing (SAST)
SAST services to help identify issues like input validation errors, buffer overflows, and insecure server configurations.
Remediation Services and Solution Review
Remediation Services to provide risk-based remediation assistance, using alternate fail-proof solutions designed by Evoke’s Security Engineers.
Application Security Assessment
An end-to-end approach that ensures overall Product/Application Security, undertaken in a phased manner.
Shift-Left Security Incorporation
Enforced earlier in the software development life cycle, these vulnerabilities are fixed to help businesses keep pace with strategic requirements.
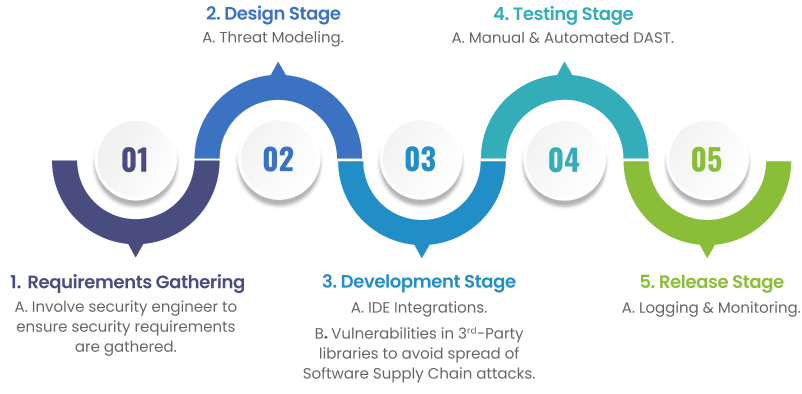
Secure SDLC Transformation
Standards Followed
- OWASP Top 10, OWASP Testing Guide, SANS 25
- OWASP Secure Coding Practices
- Software Assurance Maturity Model (SAMM)
- Common Vulnerabilities and Exposures (CVE)
- Common Vulnerability Scoring System (CVSS)
- OWASP Mobile Application Security Verification Standard
- Apple’s Security Framework
- & more… – as applicable as per project’s Technical &
Business Domain requirements




















